Página inicial do blog
SECURITY
OCT 30, 2023
How to Recognize and Dismantle a Phishing Campaign
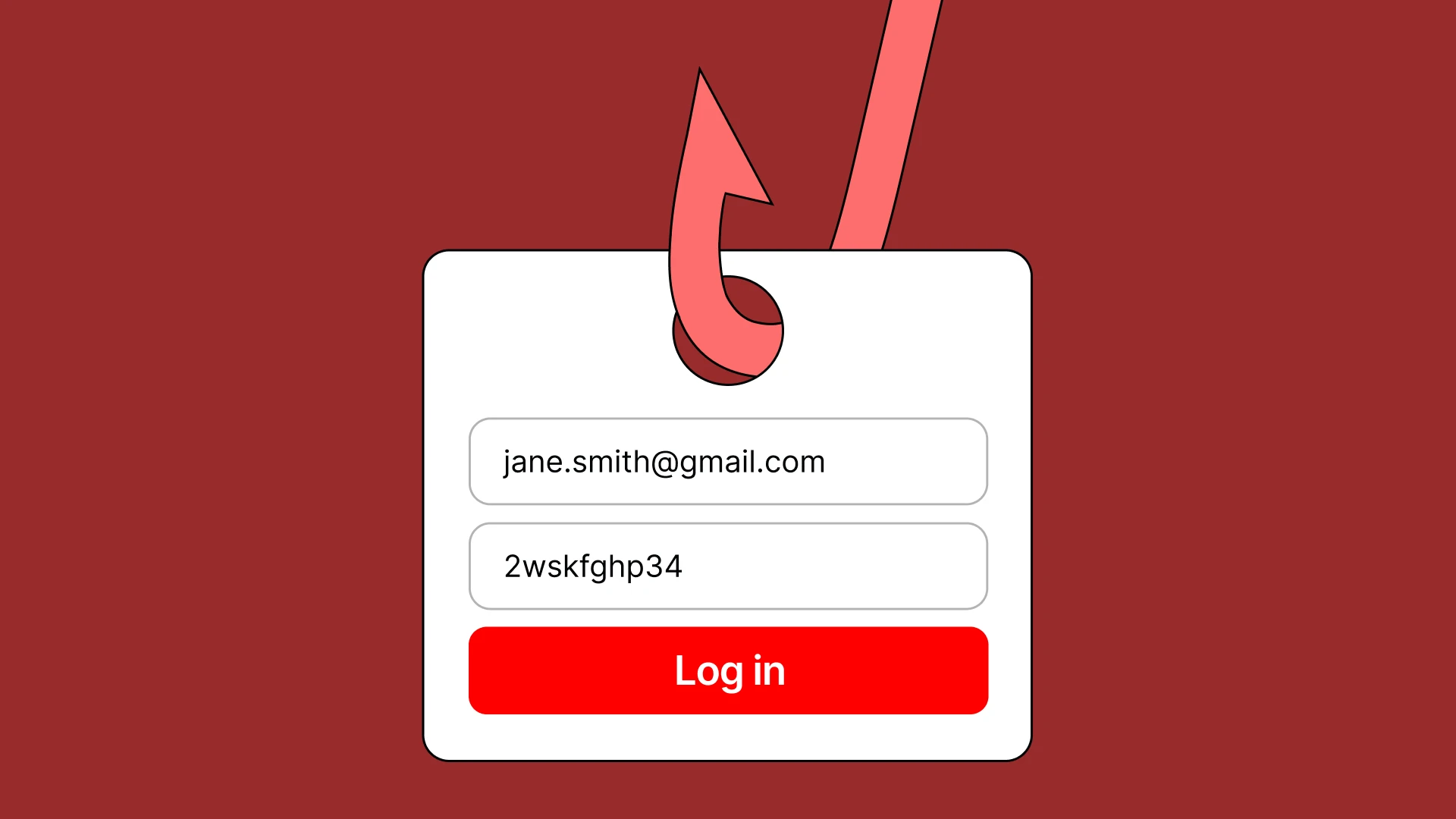
- Collaboration between our Customer Support (CS), Trust and Safety (T&S), Threat Detection and Response (TDR), and Application Security (AppSec) teams regularly leads to the identification and takedown of phishing sites.
- We believe that our varied and extensive countermeasures help keep our users protected, and we continuously monitor and adapt to new threats, ensuring our customers' assets remain secure.
- Gemini is committed to helping maintain the integrity, trustworthiness, and resilience of crypto networks, ensuring the foundations remain strong for the future of decentralized innovation.
At Gemini, ensuring the safety of our customers' assets and personal information is paramount. Since day one, we’ve operated with a security-first mindset, and we continually update our processes to stay ahead of threat actors.
In this blog post, we discuss the methods we used and actions we took against a specific phishing campaign to secure our customers’ crypto and account information, and display how we shared the information we gathered for the benefit of the wider crypto industry.
Collaboration between our Customer Support (CS), Trust and Safety (T&S), Threat Detection and Response (TDR), and Application Security (AppSec) teams regularly leads to the identification and takedown of phishing sites. To better understand attackers’ methods, we conduct investigations from a secure and isolated browsing environment to analyze phishing sites, uncovering valuable insights into their tactics.
By understanding the broader landscape of ATO attempts, we are better equipped to analyze the specific incident we encountered. Our investigations not only focus on the immediate threat but also contribute to the security community’s knowledge of threat actors, helping to identify patterns, improve control measures, and ultimately enhance our overall security posture.
Understanding Phishing Campaigns and Account Takeovers
Account takeovers (ATOs) occur when a threat actor gains unauthorized access to a customer’s account through various means, including exploiting vulnerabilities in authentication systems, leveraging misconfigurations, or social engineering. The Cyber Security and Information Security Agency (CISA) describes phishing as a form of social engineering. Phishing attacks aim to scam users out of personal and confidential information (such as your password or phone number) by abusing trust.
In most instances, phishing attacks take the form of misleading emails, text messages, or social media posts which can trick people into inadvertently responding with private information, transferring funds to the attacker’s cryptocurrency wallet, or clicking a malicious link which compromises passwords. Attackers often do this by directing a customer to a web page that is designed to look like it is owned by a trusted brand or company (i.e. Gemini). While most phishing attacks now take place online, these attacks can also occur over the phone or via offline communication channels.
The Phishing Campaign We’re Discussing Today
Today, we shed light on a specific phishing campaign in which threat actors sent Gemini customers emails and texts directing them to a fake Gemini-branded landing page.
From the fake pages, unsuspecting users would be coerced to divulge their Gemini credentials, and the nefarious actors would then attempt to gain access to the real Gemini accounts, with the ultimate aim of stealing funds.
Assessing the Tactics, Techniques, and Procedures (TTPs)
When our security team is made aware of an ongoing phishing campaign we gather all relevant information about the threat vector, take every action possible to mitigate potential damage, and get started on identifying and targeting the threat.
Analyzing phishing campaigns is central to protecting users from existing and future threats. To do this, we actively identify the malicious actors' tactics, techniques, and procedures (TTPs), as well as potential security control improvements. Below, we dive into some of the TTPs we identified during our process.
The Use of Multiple Hosting Providers to Impede Triage Efforts
While analyzing the sites the malicious emails and texts were directing users to, we determined that there was a landing phishing site and then a secondary harvesting phishing site hosted on different providers.
The landing sites had assets hosted on the CloudFlare network that linked to the harvesting phishing sites hosted on a separate network, notably azurewebsites.net. Those assets being on CloudFlare meant that tools like urlscan.io weren’t able to crawl the site to the depth needed to identify the harvesting phishing sites.

The diagram above is a simplified view of the malicious actors redirection. Victims that click on the assets hosted on Cloudflare are redirected from the landing phishing site, primarily hosted on webflow.io, to the harvesting phishing site hosted on azurewebsites.net.
We faced the same issue during our reconnaissance process, where we weren’t able to load the harvesting site in BurpSuite, an application security testing software. We were able to bypass those constraints by configuring FireFox to use BurpSite as a proxy to analyze the traffic more ergonomically. BurpSuite Proxy allowed us to retain all the HTTP that was generated while the browser interacted with the phishing sites and also provided us with the ability to search, highlight, and comment on HTTP requests.
Multiple Hosting Providers
The majority of the phishing sites we reviewed were a subdomain of the following sites. The subdomains were meant to look like they belonged to Gemini Trust Company LLC. For brevity we only include one example of each site.

Credential Harvesting Tactics
Use of Email to Transfer Harvested Credentials
While analyzing the phishing sites hosted on azurewebsites[.]net we discovered a misconfiguration that disclosed the attacker programmatically sending the unsuspecting user’s credentials and phone number from a GMail address to other GMail addresses. Those email addresses are available below:

Malicious Customer Support Chats
After the user enters a phone number, the site returns an error message and opens a chat window hosted by LiveChat, at which point the attacker requests further information from the user. During our recon we saw the chat window appear and a support agent frantically requested that we provide them with our credentials. They claimed that they needed our credentials as they were alerted that we weren’t able to log in to our account and would like to unblock us as soon as possible. We reported the following license_ids to LiveChat, which swiftly addressed the issue.

Steps We Took to Secure the Ecosystem
At Gemini, we believe that active participation is a necessary component to securing the crypto cybersecurity ecosystem. By actively engaging in cybersecurity efforts, whether you're a developer, user, or enthusiast, you contribute to the collective defense against these threats. Gemini is committed to helping maintain the integrity, trustworthiness, and resilience of crypto networks, ensuring the foundations remain for the future of decentralized innovation.
ZeroFox — Shutting Down Phishing Websites
In partnership with ZeroFox, a cloud-based cybersecurity company, we shut down over 200 phishing sites while investigating this campaign. This collaboration not only helped take down these sites but also exposed email addresses linked to the attackers, leading to further investigations.
We collaborated with ZeroFox to share this intelligence and improve the detection of malicious sites. Additionally, we reached out to providers whose infrastructure was exploited for illicit activities.
Conclusion
We believe that our varied and extensive countermeasures help keep our users protected, and acknowledge that the battle against threats on the Internet is ongoing. We continuously monitor and adapt to new threats, ensuring our customers' assets remain secure.
Gemini is dedicated to protecting its customers and the cryptocurrency community at large, and implementing new tools to support this goal. Earlier this year we introduced passkeys, which add an extra layer of security to Gemini accounts. Check out this blog to get a better understanding of how passkeys work and how they could have protected users who visited phishing sites.
Our proactive measures, collaborative efforts, and continuous vigilance against ATO attempts demonstrate our unwavering commitment to providing a secure trading environment across the crypto industry. As the crypto landscape evolves, so do our security practices, ensuring that Gemini remains a trusted platform. Your security is our priority.
Onward and Upward!
The Gemini Security Team
ARTIGOS RELACIONADOS

WEEKLY MARKET UPDATE
APR 03, 2025
Crypto Drops Following Tariff News, Circle Files for IPO, and GameStop Raises $1.5B To Buy Bitcoin

WEEKLY MARKET UPDATE
MAR 27, 2025
BlackRock Launches First European Crypto ETP, White House Narrows Tariff Strategy, and Fidelity Launches Blockchain Treasury Fund

COMPANY
MAR 26, 2025