Page d'accueil du blog
INDUSTRY
SEP 27, 2019
5 Quick Wins for Securing Your Online Accounts

Attackers have well-defined tactics for targeting your online accounts. Following these simple steps will improve your security posture.
#1: Disable SMS Account Recovery
If you don’t know if you have this enabled, there’s a good chance you do, and having it enabled is a bad idea. Attackers can get control of your phone number via phone porting, where they call your phone carrier, pretend to be you, and ask them to start sending all calls and SMS texts to a phone they own.
If this happens, and you have SMS account recovery enabled anywhere, the attacker can click “Forgot password?”, receive the verification text to their phone, and successfully log in to your email account.
Gmail, for example, provides instructions on disabling SMS account recovery here.
Note: There are many services that allow SMS account recovery. It is particularly important to remove this option from your email, though, because your email address is often how you can reset passwords for all your sites and services.
#2: Disable SMS Two-Factor Authentication
First, understand that SMS two-factor authentication is different than SMS account recovery, which I just described earlier. If you have SMS two-factor authentication turned on, it means that when you log in with your password on a site, that site sends you a text with a one-time code that you need to enter in addition to your password to log in. This is different than SMS account recovery, where you click Forgot Password? and receive a one-time code to the phone number associated with your account to reset that account’s password. No password is needed in the latter case.
You should disable SMS two-factor authentication for the same phone porting risk I outlined in point #1.
When you remove SMS two-factor authentication, it’s important to add a more secure form of two-factor authentication before signing out. You can add an authenticator application like Authy, Duo, or Google Authenticator. When you use an authenticator app, the secret one-time codes are generated on your physical device, rather than texted to your phone number. That means an attacker with control of your phone number still can’t generate the one-time codes needed to log in to your account.
Even better than adding an authenticator app is adding a security key, which I describe later.
#3: Turn off “Multi-Device” Support on your Authenticator App
However, some of these apps enable Multi-device support, which means you can enroll another device to generate the exact same codes as your current device. This allows you to have a backup device generate codes in case you lose or misplace your primary device.
Unfortunately, how you confirm that you want to add a second device is via text message to the phone number associated with your existing device. Thus, if an attacker has control of your phone number, they can take their phone, enroll it as a backup device for the authenticator app on your phone, receive the confirmation text, and successfully finish enrolling their phone’s authenticator app as your phone’s backup.
You can, and should, disable Multi-device support on your authenticator apps. Authy, as an example, explains how to do this in their support pages.
Note: Disabling multi-device support means that if you lose that device, you will have no way of logging in to your accounts (assuming you don’t have backup codes, or another form of two-factor authentication like a security key enabled). However, it also means that if an attacker gets control of your phone number, they have no way of generating these one-time codes, or enrolling their device as a “backup” to your authenticator app.
#4: Set a Voicemail PIN (or disable it!)
Voicemails are remotely accessible. That means an attacker does not need control of your phone number to listen to your voicemail messages — they just need an internet connection.
Worse yet, some services that allow SMS account recovery allow you to receive that one-time code via phone call. An automated voice recites the one-time code to you on the call, and if you don’t answer, that recording goes to your voicemail. Thus, even if an attacker doesn’t have control of your phone number, they can click Forgot password? on your account, and have the site send the one-time code for reseting your password via phone call to your phone number. If you don’t answer the call (some attackers may wait until you are asleep), and you don’t have a voicemail PIN, the attacker can remotely log in to your voicemail and listen to that one-time code.
To prevent this attack, set a voicemail PIN on your phone, or call your carrier and disable voicemail on your phone entirely.
#5: Advanced: Use a Security Key!
Some people believe that using an authenticator app like Authy or Duo instead of SMS two-factor means they are no longer vulnerable to phishing. This is untrue.
The issue with one-time numerical codes is that anyone in the world can enter them. Even if those codes can only be generated on your physical device, if you get tricked into sharing that one-time code with a fake website or fake customer support rep, an attacker can quickly use it along with your password to log in to your account from anywhere in the world.
There’s a solution to this problem called security keys on sites that implement the WebAuthN standard. A security key is a physical device that provides a cryptographic signature to confirm your identity to a site. Security keys can include: • Yubikeys • MacOS Touch ID • Feitian keys • Even more, outlined here.

Examples of security keys, provided by Yubico
Security keys have nothing to do with your phone number. The attacker would need physical access to that security key to try and authenticate as you. There’s no single-use numerical codes involved, so there is nothing you can provide a fake site or a fake customer support rep to log in to your account mistakenly. Here’s an example of logging in with MacOS Touch ID to Gemini. After entering your password, Gemini prompts you to use the Touch ID feature of your Mac to complete the log in.
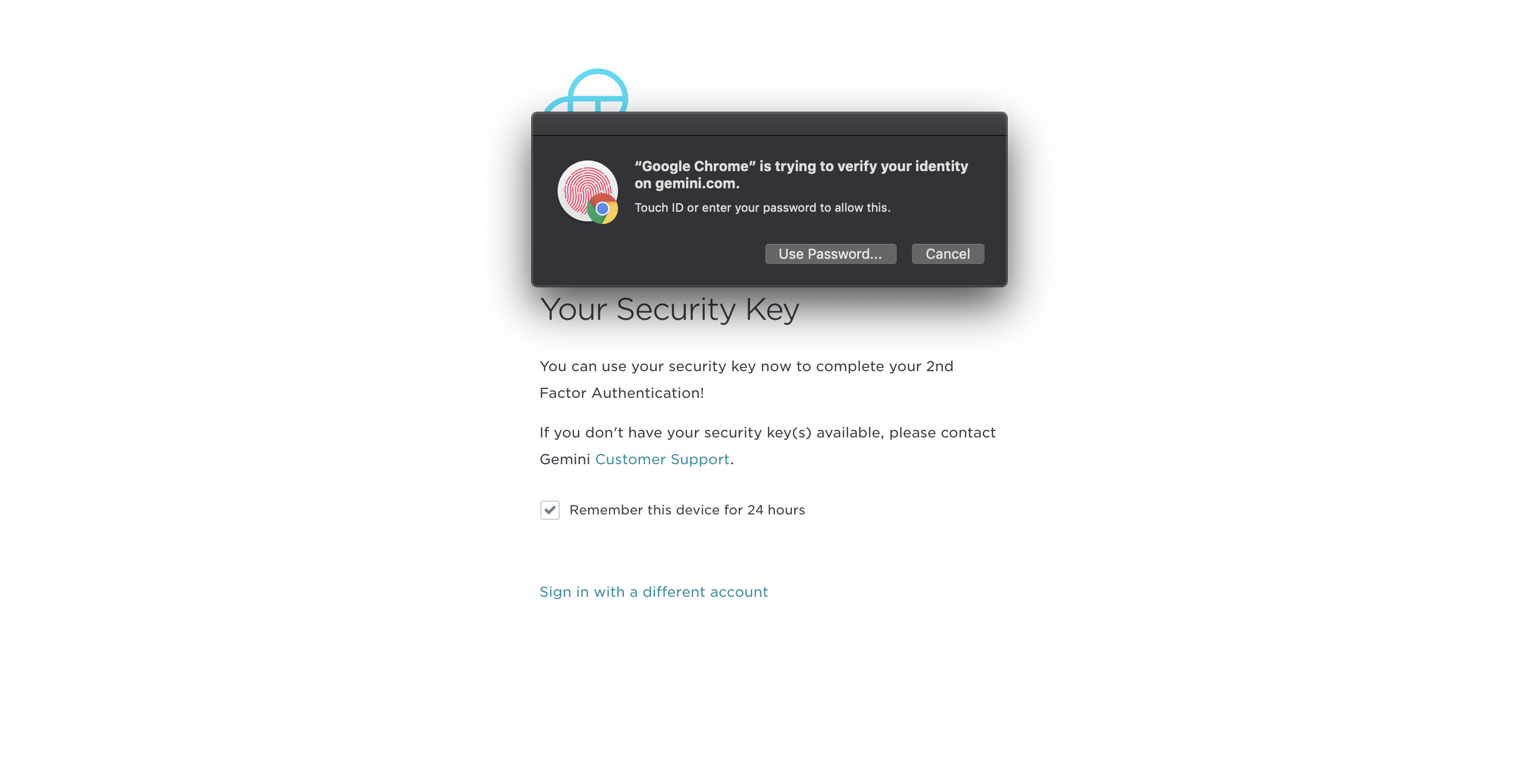
Gemini prompting for Touch ID on MacOS
Gemini became the world’s first crypto exchange and custodian to support the WebAuthn security protocol, which allows the use of security keys for logging in. You can add security keys to your Gemini account like so:
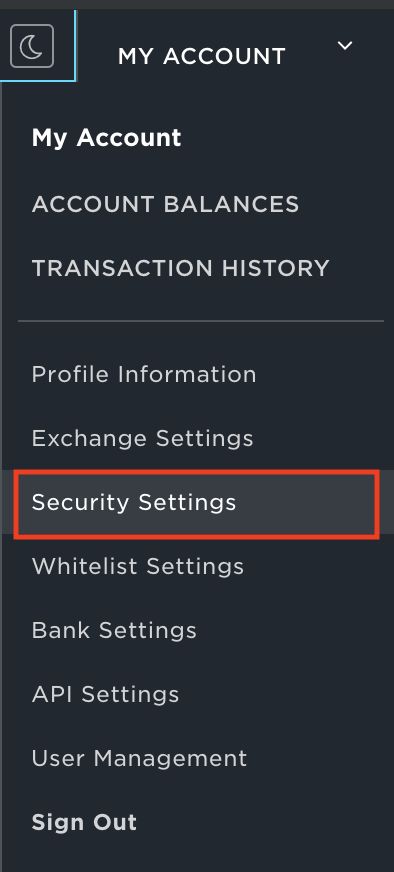
- Under My Account, select Security Settings.
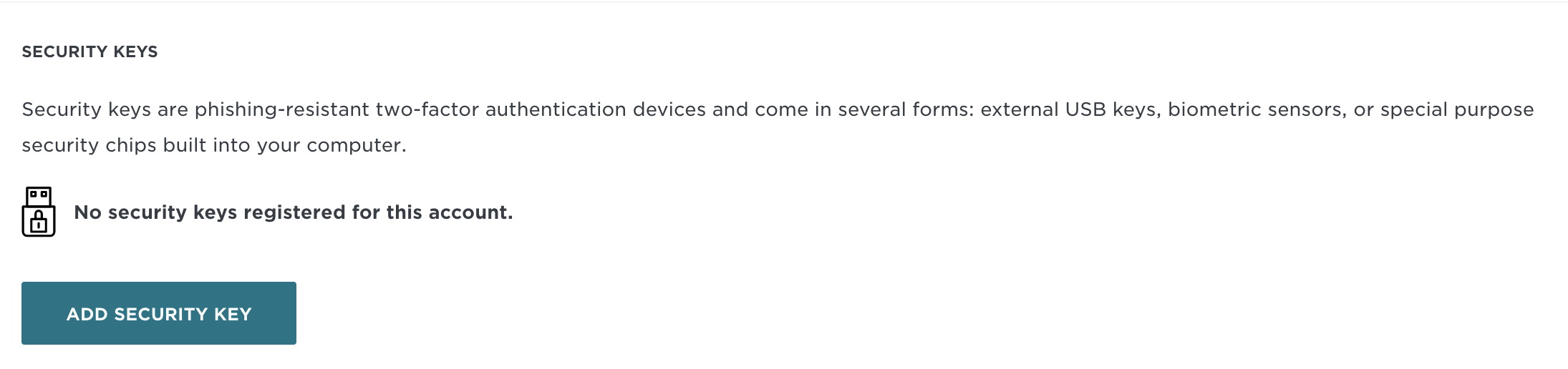
- Scroll down to Add Security Key.
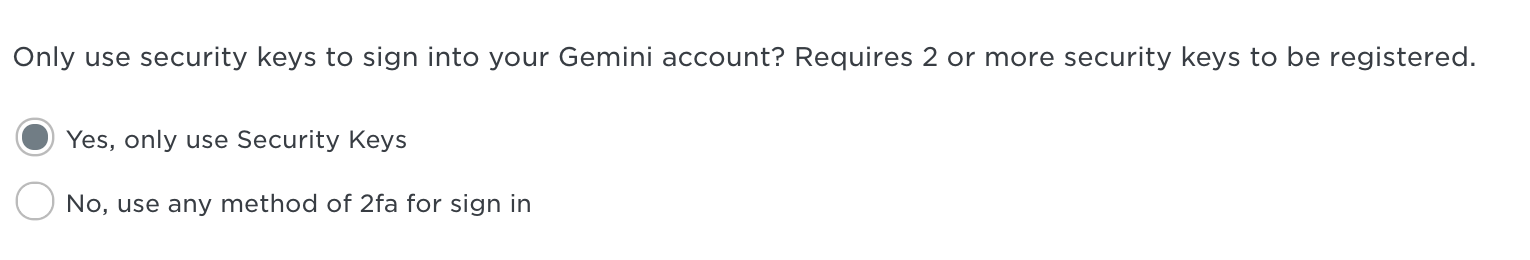
- Enroll any of the security key options mentioned in the article above. If you enroll at least two security keys, you can then select the Yes, only use Security Keys option. This ensures that you can only sign in to your Gemini account with your password and one of your security keys!
These 5 steps will improve your security posture dramatically.
Onward and Upward,
Team Gemini
ARTICLES CONNEXES

COMPANY
JAN 22, 2025
Five Crypto Predictions for 2025

COMPANY
JAN 20, 2025
Gemini Selects Malta as MiCA Hub in European Expansion Milestone

WEEKLY MARKET UPDATE
JAN 16, 2025
Crypto Rebounds After Inflation Cools More Than Expected, Blackrock Launches Canadian Spot Bitcoin ETF, and SEC Ramps Up Legal Actions
PLUS DE TEAM GEMINI
Tout afficher

COMPANY
JAN 20, 2025
Gemini Selects Malta as MiCA Hub in European Expansion Milestone

WEEKLY MARKET UPDATE
JAN 16, 2025
Crypto Rebounds After Inflation Cools More Than Expected, Blackrock Launches Canadian Spot Bitcoin ETF, and SEC Ramps Up Legal Actions

WEEKLY MARKET UPDATE
JAN 09, 2025